2023-08-04
Curve Finance is a decentralized exchange on Ethereum that allows users to swap between different types of stablecoins. On July 30, 2023, Curve Finance was hacked due to a reentrancy bug in certain pools built using the Vyper programming language, with losses reaching over $47 million.
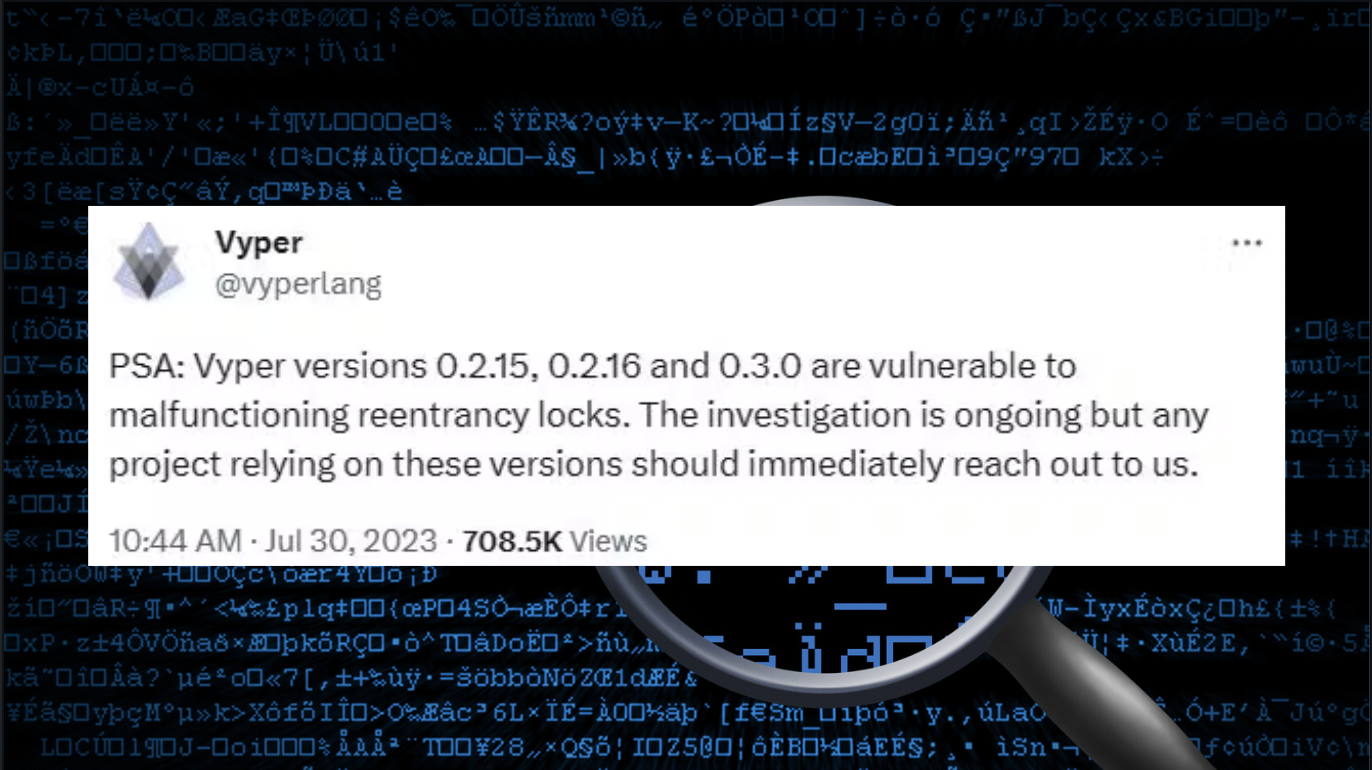
Reentrancy is a common bug that allows attackers to trick a smart contract by making repeated calls to a protocol in order to steal assets. Other projects that use the Vyper programming language could share the same vulnerability.
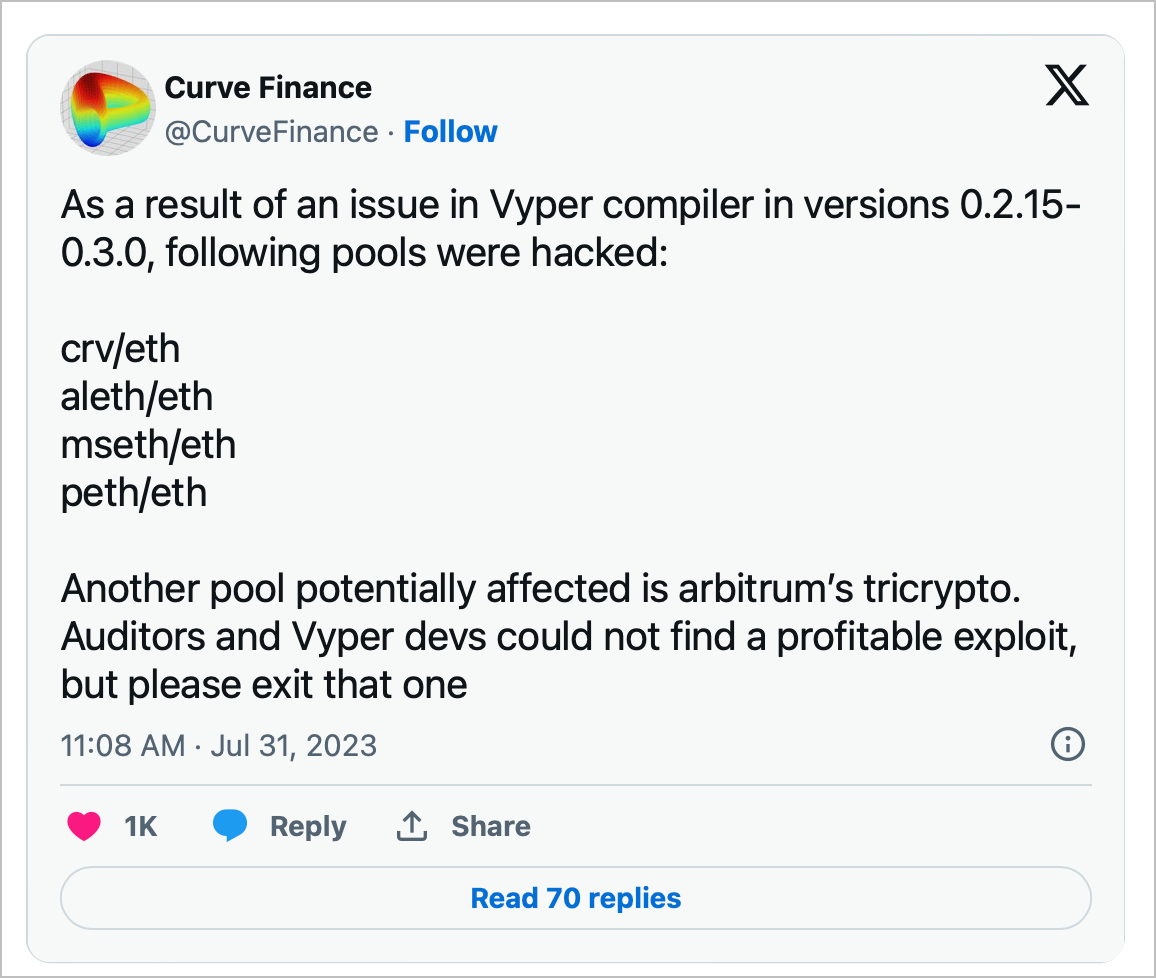
"As a result of an issue in Vyper compiler in versions 0.2.15-0.3.0, following pools were hacked: crv/eth, aleth/eth, mseth/eth, peth/eth," Curve tweeted Monday.
On the day of the hack, CRV's value dropped by 20.91%, hitting a two-month low of $0.58. The following day, it fell further to $0.48 due to concerns over $100 million loans secured by CRV and taken by Curve Finance founder Michael Egorov.
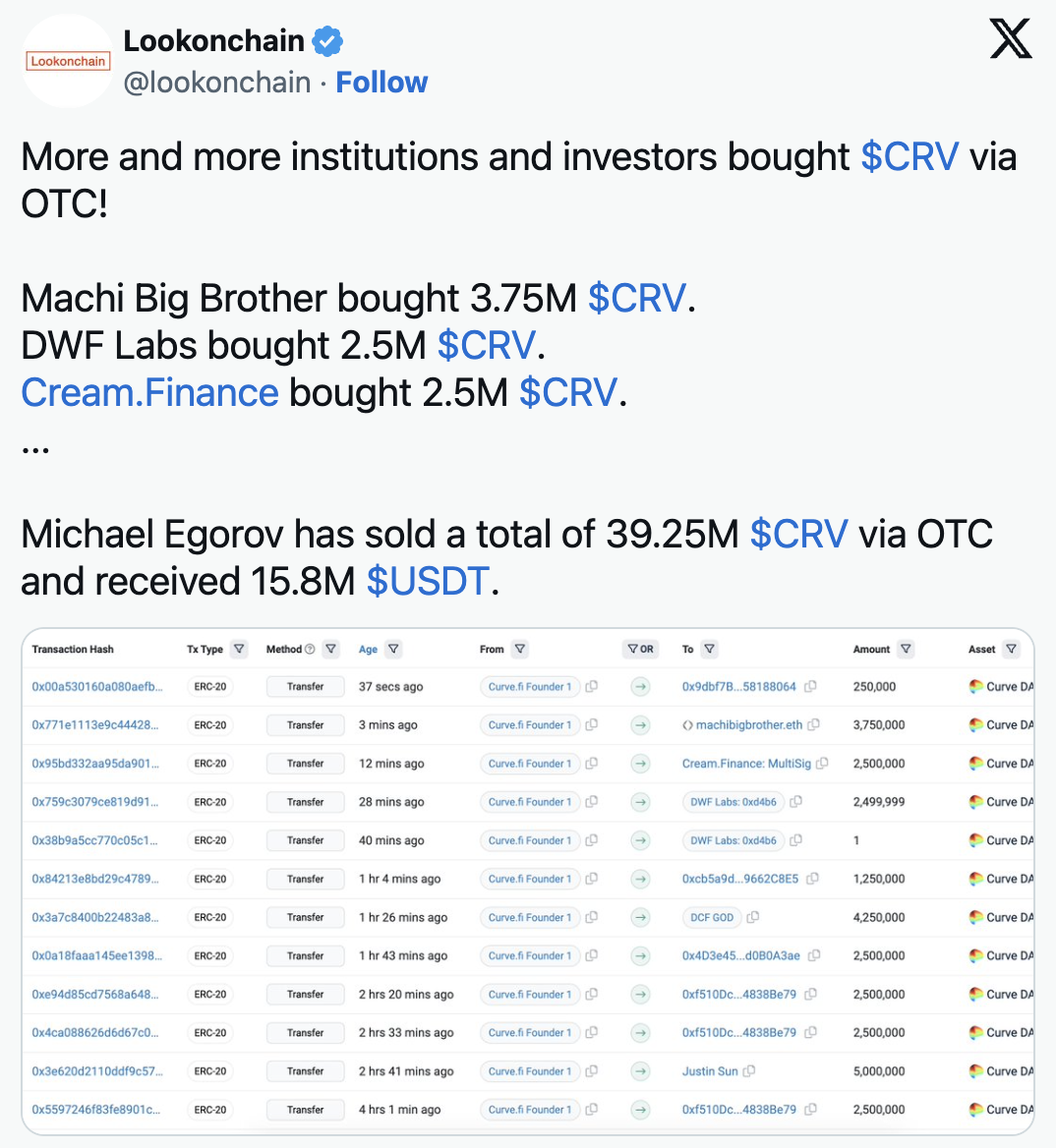
However, there are positive developments as Egorov sold 39.25 million CRV tokens at a discounted price of $0.40 to notable investors. He also made a partial repayment on his loans, reducing the liquidation risk.
Currently, Egorov's loans on Aave are at risk of liquidation if CRV drops to $0.36 or below, as per DefiLlama.
The hack has caused a sharp sell-off in the price of CRV, which poses a systemic threat to DeFi.
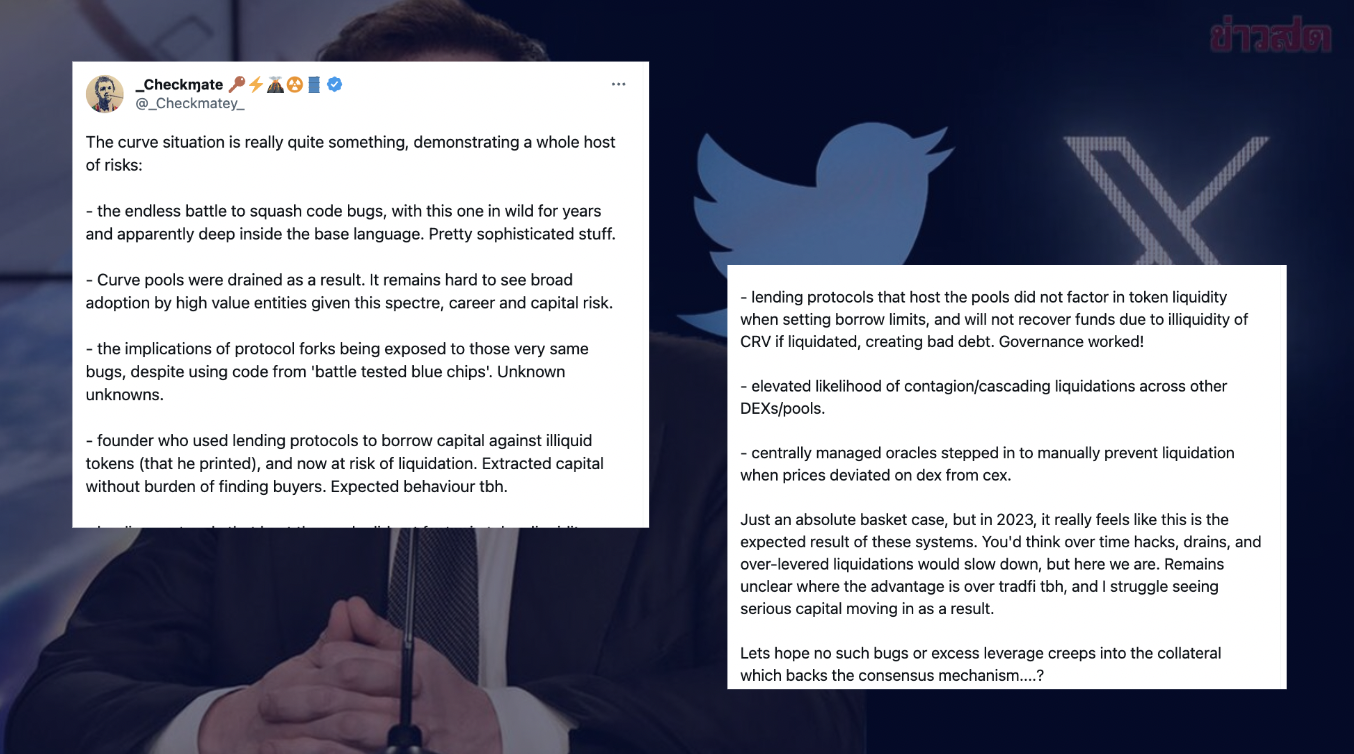
Based on the Twitter account @Checkmatey, because of DeFi protocols are complex software systems, the presence of long-standing code bugs and the draining of Curve pools underscore the challenges in maintaining software security. Moreover, the exposure of protocol forks to the same bugs despite using battle-tested code raises concerns about unknown risks. The founder's risky behavior, adds further instability. Lending protocols' oversight of token liquidity and the possibility of contagion across other DEXs/pools contribute to the complex situation. Centralized intervention to prevent liquidation shows vulnerabilities in decentralized systems. As a result, serious capital inflow into DeFi remains uncertain.
A new meme coin called BALD was launched on the Ethereum layer-2 network Base. The coin quickly gained popularity, and its price rose sharply. However, the mystery developers then pulled all of the liquidity out of the pool, effectively rug-pulling investors.
Internet sleuths have gathered evidence suggesting that SBF might be behind the rug pull. This evidence includes funding from wallets linked to FTX and Alameda Research, the involvement of BALD's developer in early voting for SushiSwap projects, certain language used in tweets, and DYDX farming activity.

On Crypto Twitter, while many hesitate to directly implicate Sam Bankman-Fried, they generally believe that the wallet owner is likely someone close to him, possibly Sam Trabucco, the co-chief executive of Alameda. The situation is still unfolding at the time of writing.

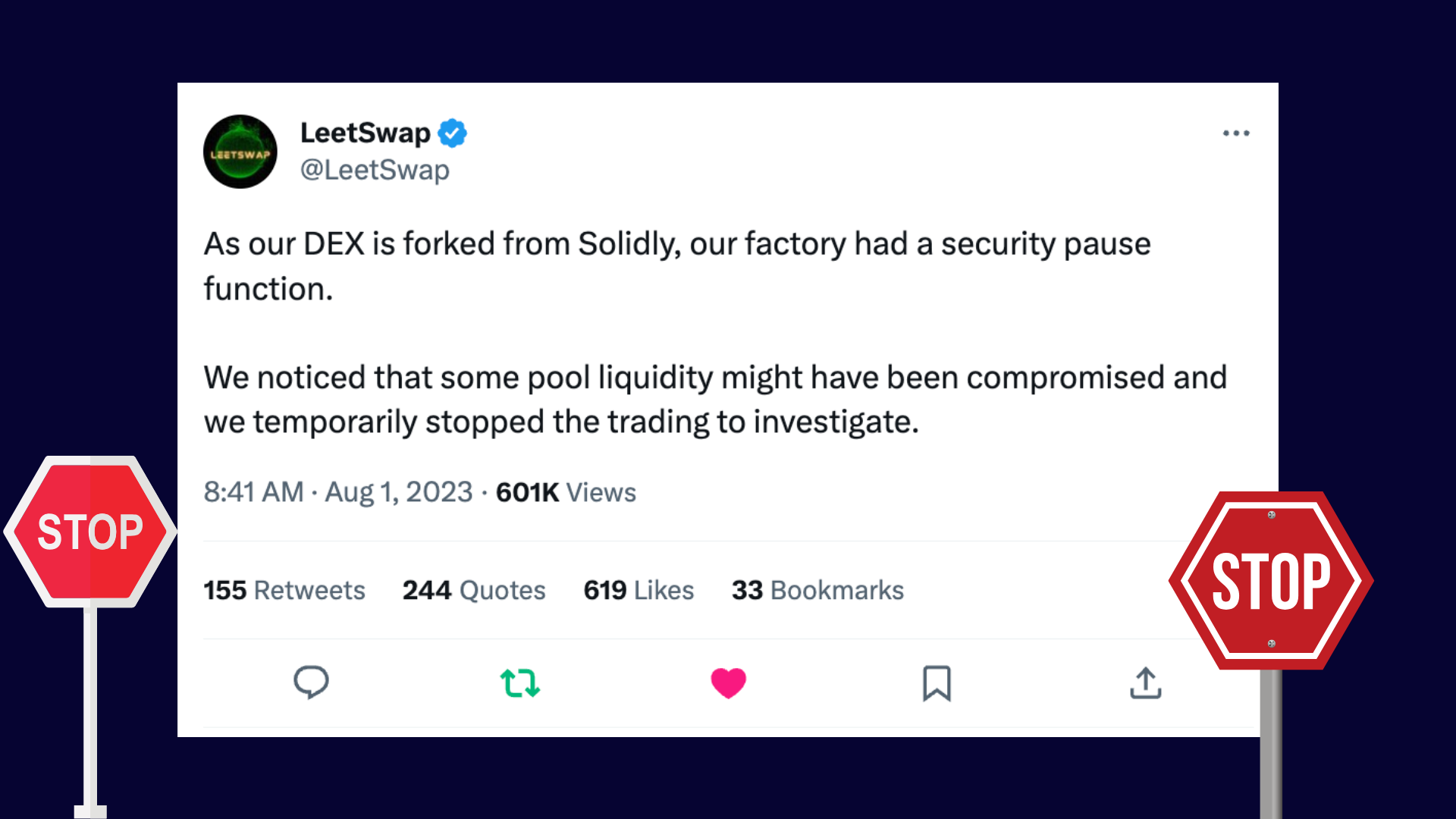
The news from the crypto world! LeetSwap, the BASE's largest DEX, hit the pause button on trading! On August 1st, LeetSwap tweeted that they noticed possible issues with their liquidity pools. They temporarily stopped trading to investigate.
LeetSwap is on the case! They noticed some liquidity pools might've been compromised and are currently investigating with on-chain security experts!
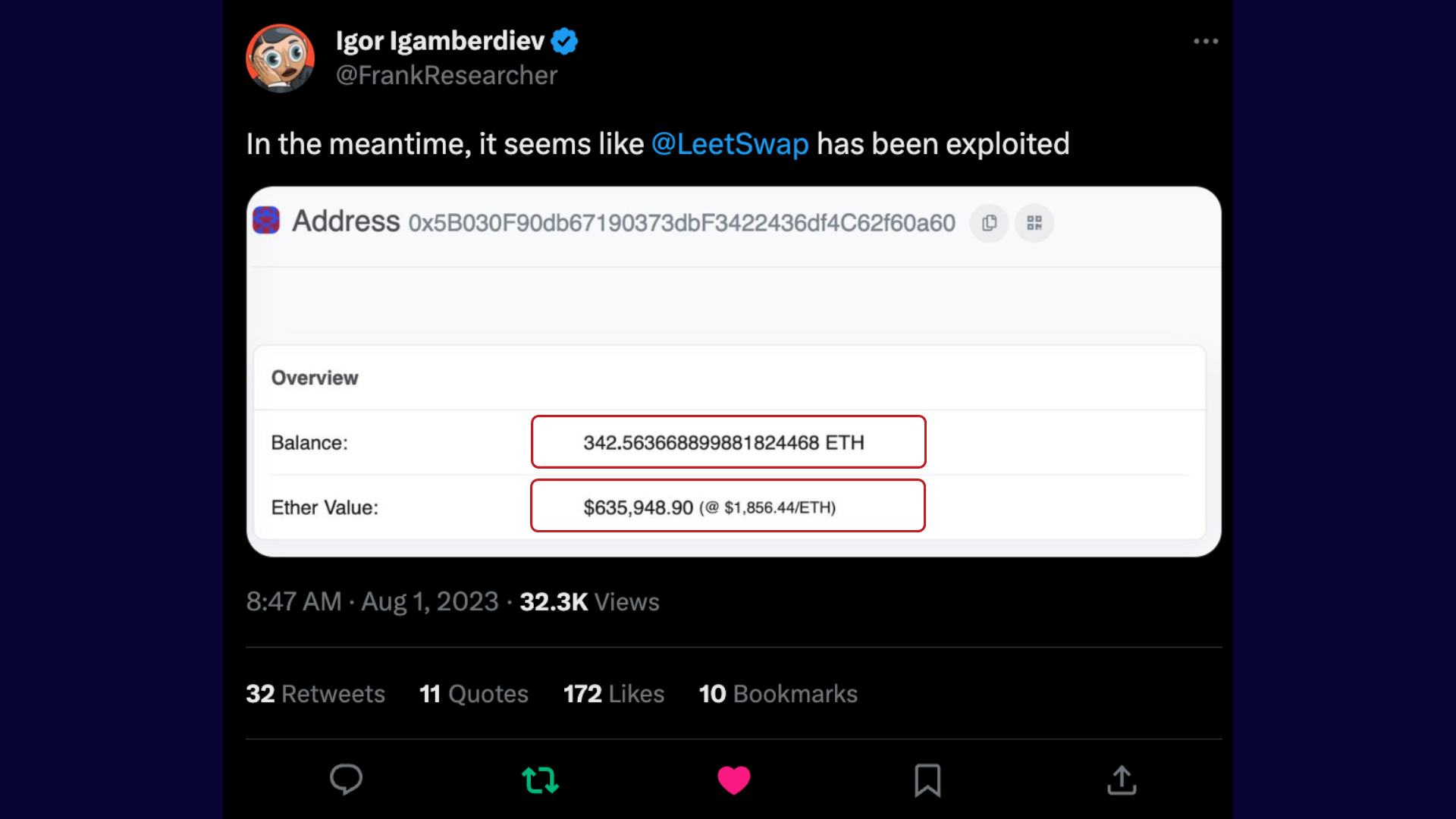
According to Igamberdiev, it appears that the attacker obtained 342.5 ETH, worth over $630,000.
Leading blockchain security firms like PeckShield, Beosin, BlockSec, and Certik confirmed the exploit and the amount taken!
ConsenSys, the blockchain technology firm, has just released a new tool called "Diligence Fuzzing" to help developers test smart contract vulnerabilities in a more secure way.
This tool introduces random and invalid data points to find potential security flaws before contracts are launched.

With over $2.8 billion lost in decentralized finance hacks last year, it's crucial to have better testing tools to prevent vulnerabilities from being exploited by attackers. The good news is that the Diligence Fuzzing tool is now available to all developers without the need for an approval process. Plus, it's integrated with the smart contract toolkit Foundry, and there's even a free version for those who want to give it a try before investing any money.
Liz Daldalian, ConsenSys security services lead explained how it works: Developers can use a machine language called "Scribble" to annotate their contracts, and the fuzzing tool will understand these annotations. By generating unexpected inputs, the tool tests whether the contract can be manipulated into unintended actions.
ConsenSys security researcher Gonçalo Sá said the tool is not a “black box fuzzer.” It does not produce completely random data. Instead, it is a “grey-box fuzzer” that employs an understanding of the program’s current state to reduce the types of data produced, increasing the tool's efficiency.
As smart contract hacks continue to be a concern, Diligence Fuzzing is a valuable tool to bolster security efforts. While it's not a guaranteed solution, it can certainly help developers write more secure contracts and reduce losses from attacks. So, it's a positive step towards minimizing potential risks in the Web3 community.
As always, we would love to hear your feedback! Please let us know your thoughts about our content, along with any suggestions for improvement through our Twitter account or Telegram channel.
Stay tuned for announcements of upcoming online events such as CryptoZombies Live Workshops and special guest online meetups.
Follow us on Twitter @CryptoZombiesHQ or signup to our mailing list or start a free course @ https://cryptozombies.io.